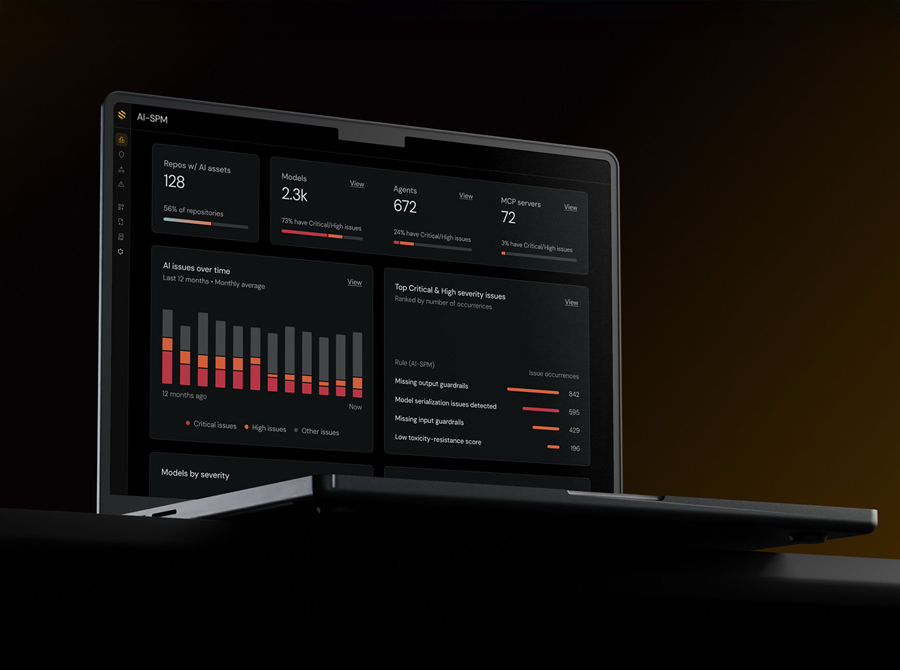
Security and DevSecOps Directors are now focused on understanding this new challenge and formulating a solid governance plan. The reality is that developers are rapidly adopting new technologies, downloading models from platforms like Hugging Face, and building on APIs without a central review process. This decentralized adoption creates a critical question: How do you secure what you can’t see and can’t control?
The Core Problem: Why Existing Tools Cannot Find Shadow AI
The existence of this unmanaged, ungoverned layer is what we define as Shadow AI, and AI Security Posture Management (AI-SPM) is the core function addressing it. Ignoring this problem, Doing Nothing, or assuming current tools are sufficient, is the biggest risk. This directly answers the fundamental security leader objection: "Is Shadow AI a real problem, or just hype?". The data confirms the reality: despite massive AI adoption, only 28% of organizations have conducted a comprehensive AI security assessment. This massive assessment gap is the foundation for the Shadow AI problem
The Blind Spots of Current Tools
Traditional security posture management tools were not built to inspect AI assets. They create significant blind spots where Shadow AI thrives.
- CSPM (Cloud Security Posture Management) systems excel at monitoring cloud buckets. However, they are limited to verifying the container's security. They cannot tell you what specific AI model is inside that container or if it possesses a known vulnerability.
- ASPM (Application Security Posture Management) is crucial for scanning code logic, but it remains blind to the unique, critical risk posed by an AI agent that is granted excessive permissions.
This lack of visibility leaves you exposed to three critical risks:
- Vulnerable Models: Developers can inadvertently deploy open-source models with known security vulnerabilities.
- Excessive Agency: An AI agent's non-human identity (NHI) may be configured with the capability to read, write, or delete sensitive data, far exceeding its required function. For example, an agent meant for summarizing public data could be compromised to access and leak internal HR records.
Data Leakage and Compliance Gaps: Without an audit trail, sensitive PII or corporate secrets can be used to train external, third-party models, violating privacy policies and preventing the creation of an AI Bill of Materials (AI-BOM) required by auditors and regulators
Defining AI-SPM: The New Security and AI Governance Framework
AI Security Posture Management (AI-SPM) is the practice and framework designed to systematically discover, assess, and remediate the security and compliance risks across your entire artificial intelligence ecosystem.
The goal is to provide true visibility into an attack surface you are currently blind to. It connects the entire AI deployment lifecycle, providing a unified view that connects:
- AI Models: Both open-source and third-party models (e.g., Anthropic, OpenAI).
- AI Agents: The non-human identities (NHIs) capable of taking autonomous actions.
- AI Infrastructure: The databases and Model Context Protocol (MCP) servers that enable deployment.
- AI Data: The flow of sensitive inputs, outputs, and training data (prompts).
The Four Pillars of AI Security
A mature AI-SPM solution transforms security from reactive to proactive, providing a comprehensive governance framework that answers four critical questions:
Total Visibility: Securing AI from Code to Cloud
To fully master AI security and truly be in control, security must shift left to where AI assets are born: in the developer's code.
Achieving this requires total visibility by scanning the entire AI lifecycle, from the developer's first commit to the production cloud environment. This is the only way to create a complete, contextual, and risk-prioritized AI inventory.
This complete view allows you to:
- Secure AI from code to cloud by inspecting Code Repositories & CI/CD Pipelines to find policy violations before deployment.
- Inventory AI infrastructure and data access points within Databases & Model Servers.
- Establish a single, unified view of every AI asset across Cloud & On-Prem Environments.
By gaining this comprehensive insight, you can align and prioritize business risk effectively, moving your organization from being at-risk to being in control and compliant.
Get Visibility Into Your AI Attack Surface
Shadow AI requires a new security paradigm. If you're building your AI strategy, you need a security partner that understands the full stack, from the ground up.
Read the AI Security Benchmark Report to understand the full scope of AI risk or connect with us to learn more.