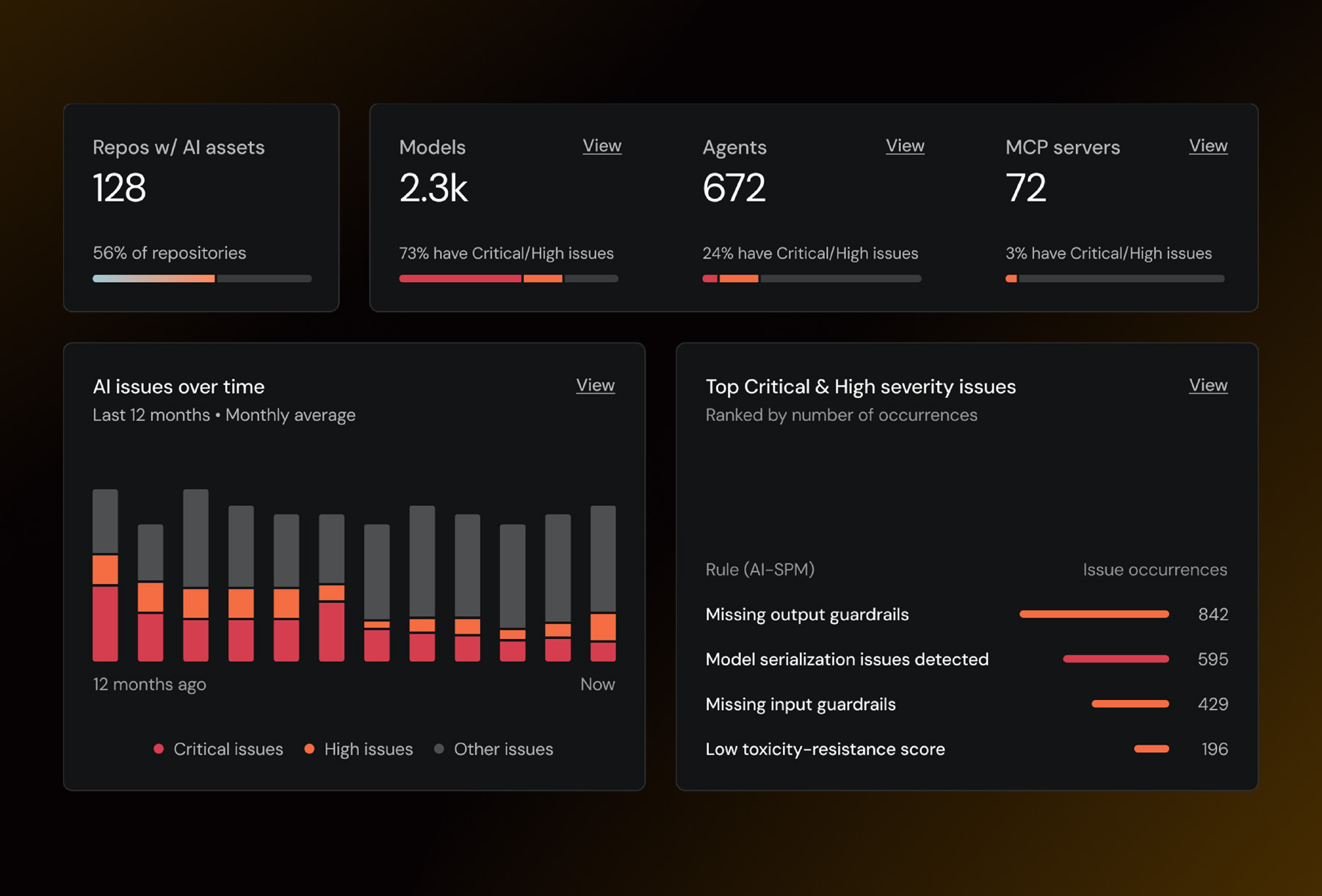
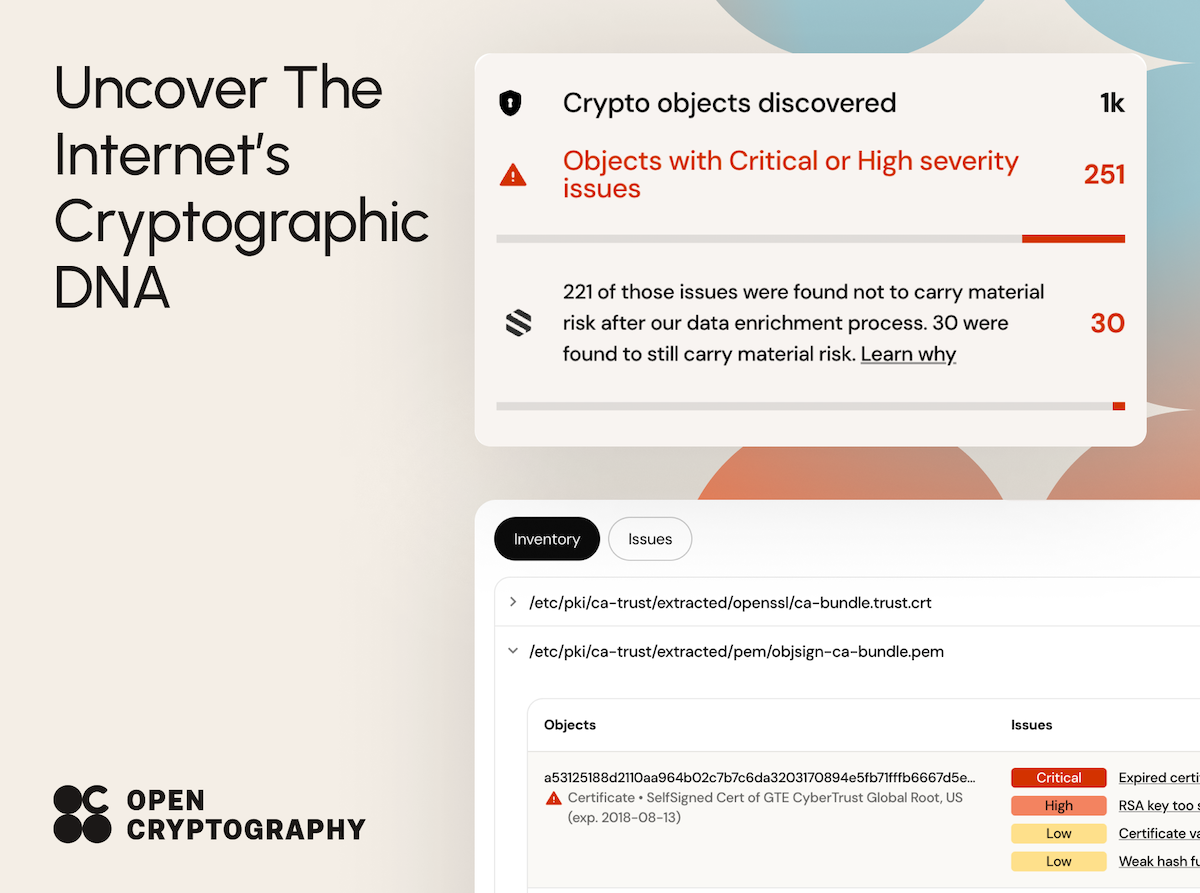
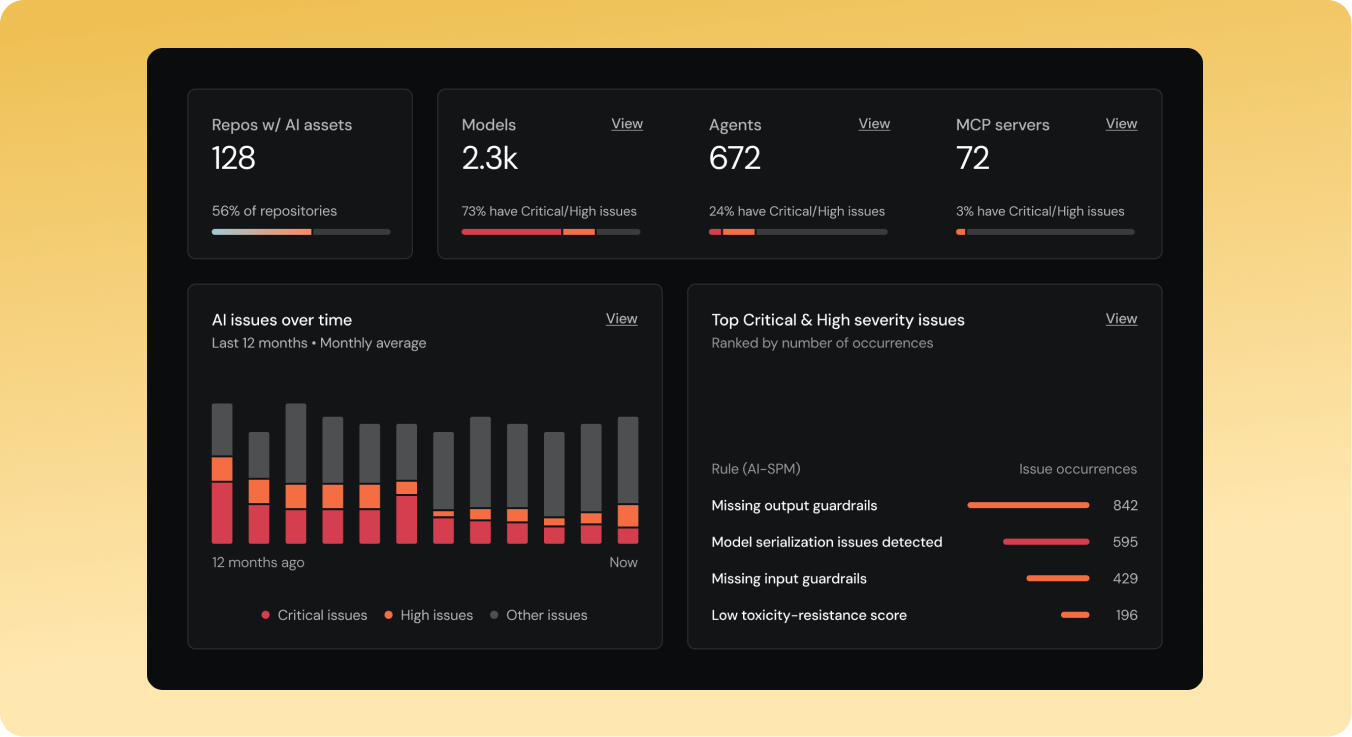
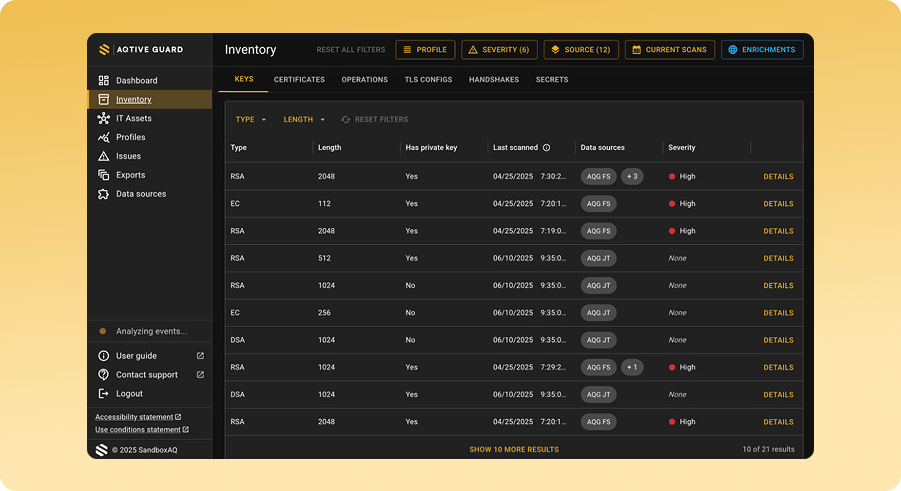
Universal visibility
Discover and inventory AI assets and encryption across your entire organization.
Intelligent risk analysis
Evaluate and prioritize AI and cryptographic risks with an expert-built analysis engine.
Automate control & remediation
Enforce security policies through automated rotation and protect keys through secure isolation.